SEE Class 10 Computer Science 2080 Npabson pre-board exam solution
NPABSON SEE PRE-QUALIFYING EXAMINATION-2080
Subject: Opt. II (Computer Science)
Full Marks: 50 Time: 1:30 hrs
Candidates are required to give their answers according to the instructions.
Attempt all the questions.
1. Answer the following questions in one sentence: [6×1=6]
a) What is a web browser?
Ans: A web browser is a software application used to access and view websites on the internet.
b) List any two commandments of computer ethics.
Ans: The following are the two commandments of computer ethics:
i) Do not use a computer to harm other people.
ii) Do not steal software or use software for which you have not paid
c) Which data type is used in MS Access to store the address of a person?
Ans: Text or Memo data type is used in MS Access to store the address of a person.
d) What is a RDBMS?
Ans: An RDBMS (Relational Database Management System) is a software system that uses a relational model to store, manage, and retrieve data in databases.
e) What is a global variable?
Ans: A global variable is declared in the main module and is accessible from any part of the program, including all modules.
f) Which mode is used to add data items into the already, existing data file in QBASIC?
Ans: APPEND mode is used to add data items into the already, existing data file in QBASIC.
2. Write appropriate technical terms for the following [2×1=2]
a) The amount of data transmitted per second through the communication channel.
Ans: Bandwidth
b) The process of making copies of data or data files to use in the event the original data or data files are lost or destroyed.
Ans: Backup
3. Write the full form for the following: [2×1=2]
a) CCTV: Closed Circuit Television
b) SIM: Subscriber Identity Module
4. Answer the following questions. [9×2=18]
a) What is computer security? Write any two software security measures.
Ans: Computer security is the process of protecting computer systems and networks from theft, damage, unauthorized access, or attacks.
Following are the two software security measures:
i) Install antivirus
ii) Regular backup
b) List four ways to stay safe on social networks.
Ans: Four ways to stay safe on social networks are as follows:
i) Create unique and complex passwords
ii) Avoid clicking on suspicious links
iii) Keep your social media apps and devices updated
iv) Accept friend requests only from people you know
c) What is m-commerce? Give two examples of digital wallets used in Nepal.
Ans: M-commerce (mobile commerce) refers to buying and selling goods and services through mobile devices such as smartphones and tablets.
Following are the two digital wallets used in Nepal:
i) eSewa and ii) Khalti
d) What is cloud computing? Write any two examples of AI.
Ans: Cloud Computing is defined as storing and accessing of data and computing services over the internet.
Following are the two examples of AI:
i) Robotics
ii) Language translation program
e) Define ring topology. Write its two advantages.
Ans: A ring topology connects devices in a closed loop, where each device is connected to two others, forming a circular chain.
The following are the two advantages of ring topology:
i) The ring topology one direction data flow ensures fewer chances of data collisions.
ii) High data transmission rate.
f) What is a foreign key? Write two properties of the primary key.
Ans: A foreign key is a column in a database table that creates a relationship between two tables by referencing the primary key of another table.
The following are the two properties of the primary key:
i) Each value must be unique to identify each row distinctly.
ii) It cannot contain NULL values.
g) Write the difference between data sorting and data filtering.
Ans: The following are the differences between data sorting and data filtering.

h) Write the difference between a database and a DBMS. Give one example of a manual database.
Ans: The following are the differences between a database and DBMS:

i) What is form? Write two uses of a form.
Ans: A form is a database object that allows users to enter, view, and edit data in a database in a more user-friendly interface.
Two uses of a form are as follows:
i) Easy to modify existing records.
ii) Create a user-friendly interface for entering new records in the table.
5. Write down the output of the given program. Show with a dry run in a table. [2]
DECLARE SUB display(s$)
CLS
s$="TOEPOHSDRA"
CALL display(s$)
END
SUB display(s$)
LET i=48
FOR c= 1 TO 4
p=I MOD 7
r$=r$+MID$(s$,p,1)
i=i-1
NEXT c
END SUB
Dry Run:
Candidates are required to give their answers according to the instructions.
Attempt all the questions.
Group 'A'
1. Answer the following questions in one sentence: [6×1=6]
a) What is a web browser?
Ans: A web browser is a software application used to access and view websites on the internet.
b) List any two commandments of computer ethics.
Ans: The following are the two commandments of computer ethics:
i) Do not use a computer to harm other people.
ii) Do not steal software or use software for which you have not paid
c) Which data type is used in MS Access to store the address of a person?
Ans: Text or Memo data type is used in MS Access to store the address of a person.
d) What is a RDBMS?
Ans: An RDBMS (Relational Database Management System) is a software system that uses a relational model to store, manage, and retrieve data in databases.
e) What is a global variable?
Ans: A global variable is declared in the main module and is accessible from any part of the program, including all modules.
f) Which mode is used to add data items into the already, existing data file in QBASIC?
Ans: APPEND mode is used to add data items into the already, existing data file in QBASIC.
2. Write appropriate technical terms for the following [2×1=2]
a) The amount of data transmitted per second through the communication channel.
Ans: Bandwidth
b) The process of making copies of data or data files to use in the event the original data or data files are lost or destroyed.
Ans: Backup
3. Write the full form for the following: [2×1=2]
a) CCTV: Closed Circuit Television
b) SIM: Subscriber Identity Module
Group 'B'
4. Answer the following questions. [9×2=18]
a) What is computer security? Write any two software security measures.
Ans: Computer security is the process of protecting computer systems and networks from theft, damage, unauthorized access, or attacks.
Following are the two software security measures:
i) Install antivirus
ii) Regular backup
b) List four ways to stay safe on social networks.
Ans: Four ways to stay safe on social networks are as follows:
i) Create unique and complex passwords
ii) Avoid clicking on suspicious links
iii) Keep your social media apps and devices updated
iv) Accept friend requests only from people you know
c) What is m-commerce? Give two examples of digital wallets used in Nepal.
Ans: M-commerce (mobile commerce) refers to buying and selling goods and services through mobile devices such as smartphones and tablets.
Following are the two digital wallets used in Nepal:
i) eSewa and ii) Khalti
d) What is cloud computing? Write any two examples of AI.
Ans: Cloud Computing is defined as storing and accessing of data and computing services over the internet.
Following are the two examples of AI:
i) Robotics
ii) Language translation program
e) Define ring topology. Write its two advantages.
Ans: A ring topology connects devices in a closed loop, where each device is connected to two others, forming a circular chain.
The following are the two advantages of ring topology:
i) The ring topology one direction data flow ensures fewer chances of data collisions.
ii) High data transmission rate.
f) What is a foreign key? Write two properties of the primary key.
Ans: A foreign key is a column in a database table that creates a relationship between two tables by referencing the primary key of another table.
The following are the two properties of the primary key:
i) Each value must be unique to identify each row distinctly.
ii) It cannot contain NULL values.
g) Write the difference between data sorting and data filtering.
Ans: The following are the differences between data sorting and data filtering.

h) Write the difference between a database and a DBMS. Give one example of a manual database.
Ans: The following are the differences between a database and DBMS:

i) What is form? Write two uses of a form.
Ans: A form is a database object that allows users to enter, view, and edit data in a database in a more user-friendly interface.
Two uses of a form are as follows:
i) Easy to modify existing records.
ii) Create a user-friendly interface for entering new records in the table.
5. Write down the output of the given program. Show with a dry run in a table. [2]
DECLARE SUB display(s$)
CLS
s$="TOEPOHSDRA"
CALL display(s$)
END
SUB display(s$)
LET i=48
FOR c= 1 TO 4
p=I MOD 7
r$=r$+MID$(s$,p,1)
i=i-1
NEXT c
END SUB
Dry Run:
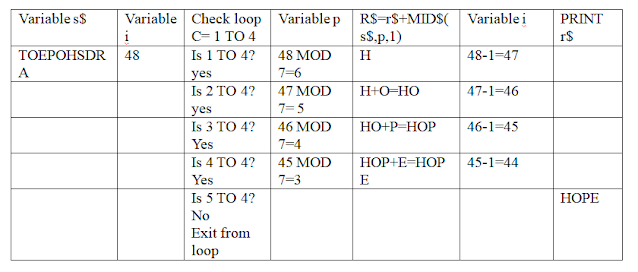
Final Output:
HOPE
6. Re-write the given program after correcting the bugs. [2]
REM program to add records to an existing file "student.dat"
OPEN "student.dat" FOR APPEND AS #1
DO
CLS
INPUT "Enter name:";n$
INPUT "Enter address:";ad$
INPUT "Enter total marks:"tm$
COPY #1, n$, ad$, tm
INPUT "Do you want to add more records? Press y or N:";ch$
LOOP WHILE UCASE$(ch$)<>"Y"
CLOSE "student.dat"
END
Ans: Debugged program
REM program to add records to an existing file "student.dat"
OPEN "student.dat" FOR APPEND AS #1
DO
CLS
INPUT "Enter name:";n$
INPUT "Enter address:";ad$
INPUT "Enter total marks:"tm
WRITE #1, n$, ad$, tm
INPUT "Do you want to add more records? Press y or N:";ch$
LOOP WHILE UCASE$(ch$)="Y"
CLOSE #1
END
7. Study the given program and answer the questions follow. [2]
DECLARE FUNCTION calculate(x,y)
CLS
INPUT "Enter a multi-digit number:";n
LET s=calculate(n,t)
PRINT "The sum=";s
END
FUNCTION calculate (x,y)
WHILE x<> 0
r= x MOD 10
y=y+r
x=x\10
WEND
calculate=y
END FUNCTION
a) List formal parameters and real parameters used in the above program.
Ans: Formal parameters : x and y
Real parameter : n and t
b) What is the purpose of the above program?
Ans: The purpose of the above program is to display the sum of input digits.
8) Perform the following as indicated [4×1=4]
a) (11101011)2=(?)8
b) (65)10=(?)2

c) (11101)2 + (11011)2 – (11110)2
d) (111011)2 ÷ (11)2
9. a) Write a program in QBASIC to find out the sum of three numbers using the SUB procedure and the average of three numbers using the FUNCTION procedure. [4]
DECLARE SUB sum (a, b, c)
DECLARE FUNCTION average (a, b, c)
CLS
INPUT "Enter three numbers: "; a, b, c
CALL sum(a, b, c)
PRINT average(a, b, c)
END
FUNCTION average (a, b, c)
average = (a + b + c) / 3
END FUNCTION
SUB sum (a, b, c)
s = a + b + c
PRINT "sum"; s
END SUB
b) A sequential data file, "record.dat" contains several records with data items name, address, age, and phone number. Write a program to display all the records of students whose age is greater than or equal to 18. [4]
Ans:OPEN "record.dat" FOR INPUT AS #1
CLS
DO WHILE NOT EOF(1)
INPUT 31, n$,a$,age,ph
IF age>=18 THEN PRINT n$, a$, age, ph
LOOP
CLOSE #1
END
10. Write a program in C language to input the length of the three rods and display whether the triangle can be formed by those rods or not. [4]
Ans:
#include<stdio.h>
int main()
{
float a,b,c;
printf("Enter length of three rods");
scanf("%f%f%",&a,&b,&c);
if(a+b>c && a+c>b && b+c>a)
printf("The triangle can be formed");
else
printf("the triangle cannot be formed");
return();
}
OR
Write a program in C language to declare whether the given number is "positive", "negative" or "zero" [4] #include<stdio.h>
int main()
{
int n;
printf("Enter any number\n");
scanf("%d",&n);
if(n>0)
printf("Positve number");
else if(n<0)
printf("Negative number");
else
printf("Zero");
return 0;
}
You may also read:
Pabson see pre-board exam 2079 computer solved








.png)




.png)



.png)

Amazing
ReplyDelete