PABSON SEE PRE-QUALIFYING EXAM-2080 COMPUTER SET 2 SOLVED

Subject: Opt. II (Computer Science)
g) What is the primary key? Write its importance.
Ans: A primary key is a special field within a table that uniquely identifies each record.
The following are the importance of the primary key:
i) It avoids the duplicate data.
ii) . Enables the establishment of relationships between tables
h) What is the data type? List any two data types of MS Access.
Ans: Data type refers to the classification of data stored in a field, specifying the kind of data it can hold
Two data types of MS-Access are:
i) Text
ii) Number
i) Why update query is necessary in the database system? Give reason.
Ans: An update query is necessary in the database for the following reasons.
i) Update query allows for the correction of inaccurate data that may have been entered mistakenly.
ii) Update query helps in maintaining the integrity and consistency of related data across different tables within the database.
5. Write the output of the given program. (Workout with dry-run) [2]
DECLARE SUB show ()
CLS
CALL show
END
SUB show
FOR i=1 TO 7 STEP 3
s=s+i^3
NEXT i
PRINT s
END SUB
Dry Run:
Final Output:
Pabson see pre-board exam 2079 computer solved
Full Marks: 50 Time: 1:30 hrs
Candidates are required to give their answers according to the instructions.
Attempt all the questions.
1. Answer the following questions in one sentence: [6×1=6]
a) Which connector is used with coaxial cable?
Ans: BNC connector is used with coaxial cable.
b) Why is data decryption necessary?
Ans: Data decryption is necessary to access and interpret encrypted information for authorized use.
c) Which data types are used to store graphics and numeric characters in MS Access?
Ans: To store graphics OLE data type and to store numeric characters NUMBER data types are used in MS Access.
d) List any two objects of MS Access.
Ans: Table and Query are two objects of MS Access.
e) What is the function of MOD in Qbasic?
Ans: In QBasic, the MOD function returns the remainder of a division between two numbers.
f) Write the name of unary operators used in C-Language.
Ans: Following are the names of unary operators used in C- Language:
++ (Increment operator)
-- (Decrement operator)
2. Write appropriate technical terms for the following. [2×1=2]
a) The protection of computer systems and sensitive information from ,unauthorized access, theft or damage.
Ans: Cybersecurity
b) The internet tool which is used to upload/download data.
Ans: FTP
3. Write the full form of the following: [2×1=2]
a) VOIP: Voice Over Internet Protocol
b) ISDN: Integrated Service Digital Network
4. Answer the following questions: [9×2=18]
a) What is topology? Draw the figure of star topology.
Ans: A network topology is the physical and logical arrangement of nodes and connections in a network.
b) What is cyber-ethics? List any two cybercrimes.
Ans: Cyber ethics are the moral principles guiding responsible behavior in the digital world, protecting individuals, data, and society.
Following are the two cybercrimes:
i) Phishing
ii) Cyberbullying
c) What is hardware security? Write any two measures of software security.
Ans: Hardware security refers to the protection of physical computer components and their functionalities from unauthorized access, theft, or damage.
The following are the two measures of software security:
i) Antivirus and antimalware software
ii) Use strong passwords
d) What is e-government? Give any two examples.
Ans: E-government uses technology (websites, apps, etc.) to deliver government services and information to citizens and businesses.
Following are the two examples of e-government:
i) Online tax filing
ii) Renewing licenses online
e) Define cloud computing with an example.
Ans: Cloud Computing is defined as storing and accessing of data and computing services over the internet.
Following are the examples of cloud computing:
i) Dropbox
ii) Google Drive
iii) IBM Cloud
iv) iCloud
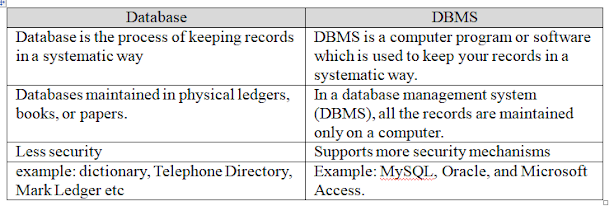
f) Differentiate between database and DBMS.
Ans:
Candidates are required to give their answers according to the instructions.
Attempt all the questions.
Group 'A'
1. Answer the following questions in one sentence: [6×1=6]
a) Which connector is used with coaxial cable?
Ans: BNC connector is used with coaxial cable.
b) Why is data decryption necessary?
Ans: Data decryption is necessary to access and interpret encrypted information for authorized use.
c) Which data types are used to store graphics and numeric characters in MS Access?
Ans: To store graphics OLE data type and to store numeric characters NUMBER data types are used in MS Access.
d) List any two objects of MS Access.
Ans: Table and Query are two objects of MS Access.
e) What is the function of MOD in Qbasic?
Ans: In QBasic, the MOD function returns the remainder of a division between two numbers.
f) Write the name of unary operators used in C-Language.
Ans: Following are the names of unary operators used in C- Language:
++ (Increment operator)
-- (Decrement operator)
2. Write appropriate technical terms for the following. [2×1=2]
a) The protection of computer systems and sensitive information from ,unauthorized access, theft or damage.
Ans: Cybersecurity
b) The internet tool which is used to upload/download data.
Ans: FTP
3. Write the full form of the following: [2×1=2]
a) VOIP: Voice Over Internet Protocol
b) ISDN: Integrated Service Digital Network
Group 'B'
4. Answer the following questions: [9×2=18]
a) What is topology? Draw the figure of star topology.
Ans: A network topology is the physical and logical arrangement of nodes and connections in a network.
b) What is cyber-ethics? List any two cybercrimes.
Ans: Cyber ethics are the moral principles guiding responsible behavior in the digital world, protecting individuals, data, and society.
Following are the two cybercrimes:
i) Phishing
ii) Cyberbullying
c) What is hardware security? Write any two measures of software security.
Ans: Hardware security refers to the protection of physical computer components and their functionalities from unauthorized access, theft, or damage.
The following are the two measures of software security:
i) Antivirus and antimalware software
ii) Use strong passwords
d) What is e-government? Give any two examples.
Ans: E-government uses technology (websites, apps, etc.) to deliver government services and information to citizens and businesses.
Following are the two examples of e-government:
i) Online tax filing
ii) Renewing licenses online
e) Define cloud computing with an example.
Ans: Cloud Computing is defined as storing and accessing of data and computing services over the internet.
Following are the examples of cloud computing:
i) Dropbox
ii) Google Drive
iii) IBM Cloud
iv) iCloud
f) Differentiate between database and DBMS.
Ans:
g) What is the primary key? Write its importance.
Ans: A primary key is a special field within a table that uniquely identifies each record.
The following are the importance of the primary key:
i) It avoids the duplicate data.
ii) . Enables the establishment of relationships between tables
h) What is the data type? List any two data types of MS Access.
Ans: Data type refers to the classification of data stored in a field, specifying the kind of data it can hold
Two data types of MS-Access are:
i) Text
ii) Number
i) Why update query is necessary in the database system? Give reason.
Ans: An update query is necessary in the database for the following reasons.
i) Update query allows for the correction of inaccurate data that may have been entered mistakenly.
ii) Update query helps in maintaining the integrity and consistency of related data across different tables within the database.
5. Write the output of the given program. (Workout with dry-run) [2]
DECLARE SUB show ()
CLS
CALL show
END
SUB show
FOR i=1 TO 7 STEP 3
s=s+i^3
NEXT i
PRINT s
END SUB
Dry Run:
Final Output:
408
6. Re-write the given program after correcting bugs. [2]
REM to display records of students from sequential data file.
OPEN "student.dat" FOR INP A #1
PRINT "Sno", "Name", "Address", "Class", "Section"
WHILE NOT EOF
INPUT #1, sn,n$, ad$, c,se$
PRINT sn,n$,ad$,c,se$
NEXT
CLOSE #1
STOP
Ans: Debugged program:
REM to display records of students from sequential data file.
OPEN "student.dat" FOR INPUT A #1
PRINT "Sno", "Name", "Address", "Class", "Section"
WHILE NOT EOF(1)
INPUT #1, sn,n$, ad$, c,se$
PRINT sn,n$,ad$,c,se$
WEND
CLOSE #1
END
7. Study the following program and answer the given questions. [2]
DECLARE FUNCTION num(n)
CLS
FOR I = 1 TO 5
READ n
z=num(n)
s=s+z
NEXT i
PRINT s
DATA 11, 14,16,5,7
END
FUNCTION num(n)
IF n MOD 2 = 0 THEN num=n
END FUNCTION
a) List the library function used in the above program.
Ans: There is no library function used in the above program.
b) Write the name of the function used in the above program.
Ans: num
8. Calculate or convert as per instructions. [4×1=4]
a) (101110111)2=(?)8
b) (248)10=(?)2

c) (1101)2×(110)2-(1011)2
d) (1011101)2÷(101)

9.a) Write a program to print circumference of a circle using SUB and volume of a cylinder using FUNCTION. [Hints: 2×22/7×r, VC=22/7×r^2×2]
DECLARE SUB cir (r)
DECLARE FUNCTION vc (r, h)
CLS
INPUT "Enter radius and height:"; r, h
CALL cir(r)
PRINT vc(r, h)
END
SUB cir (r)
c = 2 * 22 / 7 * r
PRINT "Circumference of a circle:"; c
END SUB
FUNCTION vc (r, h)
vc = 22 / 7 * r ^ 2 * h
END FUNCTION
OPEN "employee.dat" FOR INPUT AS #1
DO WHILE NOT EOF(1)
INPUT #1, sn, n$,a$,p$,s
IF s>5000 THEN PRINT sn, n$, a$, p$, s
LOOP
CLOSE #1
END
10. a) Write a program to read any three integer numbers from the keyboard and find the smallest number using C language. [4]
Ans:
#include<stdio.h>
int main()
{
int a,b,c,s;
printf("enter any three numbers: ");
scanf("%d%d%d",&a,&b,&c);
if(a<b && a<c)
{
s=a;
}
else if(b<a && b<c)
{
s=b;
}
else
{
s=c;
}
printf("Smallest no=%d",s);
}
OR
Write a program to print 10 natural numbers using C Language.
#include<stdio.h>
int main()
{
int x;
for(x=1;x<=10;x++)
{
printf("%d\t",x);
}
return 0;
}
6. Re-write the given program after correcting bugs. [2]
REM to display records of students from sequential data file.
OPEN "student.dat" FOR INP A #1
PRINT "Sno", "Name", "Address", "Class", "Section"
WHILE NOT EOF
INPUT #1, sn,n$, ad$, c,se$
PRINT sn,n$,ad$,c,se$
NEXT
CLOSE #1
STOP
Ans: Debugged program:
REM to display records of students from sequential data file.
OPEN "student.dat" FOR INPUT A #1
PRINT "Sno", "Name", "Address", "Class", "Section"
WHILE NOT EOF(1)
INPUT #1, sn,n$, ad$, c,se$
PRINT sn,n$,ad$,c,se$
WEND
CLOSE #1
END
7. Study the following program and answer the given questions. [2]
DECLARE FUNCTION num(n)
CLS
FOR I = 1 TO 5
READ n
z=num(n)
s=s+z
NEXT i
PRINT s
DATA 11, 14,16,5,7
END
FUNCTION num(n)
IF n MOD 2 = 0 THEN num=n
END FUNCTION
a) List the library function used in the above program.
Ans: There is no library function used in the above program.
b) Write the name of the function used in the above program.
Ans: num
Group 'C'
8. Calculate or convert as per instructions. [4×1=4]
a) (101110111)2=(?)8
b) (248)10=(?)2

c) (1101)2×(110)2-(1011)2
d) (1011101)2÷(101)

9.a) Write a program to print circumference of a circle using SUB and volume of a cylinder using FUNCTION. [Hints: 2×22/7×r, VC=22/7×r^2×2]
DECLARE SUB cir (r)
DECLARE FUNCTION vc (r, h)
CLS
INPUT "Enter radius and height:"; r, h
CALL cir(r)
PRINT vc(r, h)
END
SUB cir (r)
c = 2 * 22 / 7 * r
PRINT "Circumference of a circle:"; c
END SUB
FUNCTION vc (r, h)
vc = 22 / 7 * r ^ 2 * h
END FUNCTION
b) A sequential data file "employee.dat" has some records with field's serial number, name, address, post and salary for the number of employee. Write a program to display all the records of those employees whose salary is more than Rs. 50000.
OPEN "employee.dat" FOR INPUT AS #1
DO WHILE NOT EOF(1)
INPUT #1, sn, n$,a$,p$,s
IF s>5000 THEN PRINT sn, n$, a$, p$, s
LOOP
CLOSE #1
END
10. a) Write a program to read any three integer numbers from the keyboard and find the smallest number using C language. [4]
Ans:
#include<stdio.h>
int main()
{
int a,b,c,s;
printf("enter any three numbers: ");
scanf("%d%d%d",&a,&b,&c);
if(a<b && a<c)
{
s=a;
}
else if(b<a && b<c)
{
s=b;
}
else
{
s=c;
}
printf("Smallest no=%d",s);
}
OR
Write a program to print 10 natural numbers using C Language.
#include<stdio.h>
int main()
{
int x;
for(x=1;x<=10;x++)
{
printf("%d\t",x);
}
return 0;
}
You may also Read:
SEE Computer Science New Model Questions 2079(2023) With Answer







.png)





.png)

.png)

No comments:
Post a Comment